catch me if you can
F12拿到flag
actf{y0u_caught_m3!_0101ff9abc2a724814dfd1c85c766afc7fbd88d2cdf747d8d9ddbf12d68ff874}
Celeste Speedrunning Association
看题目意思好像要时间破个记录,访问/play路由有个按钮,点了后告诉我没有破记录,用hackbar看一眼有个POST参数start,猜测是通过当前时间减去这个start的时间值来算记录时间的,那就把start的值改大一点,让时间是负的就可以拿到flag
actf{wait_until_farewell_speedrun}
shortcircuit
随便传入账号密码不对,hackbar也没显示传参,F12查看源码发现一段js
const swap = (x) => {
let t = x[0]
x[0] = x[3]
x[3] = t
t = x[2]
x[2] = x[1]
x[1] = t
t = x[1]
x[1] = x[3]
x[3] = t
t = x[3]
x[3] = x[2]
x[2] = t
return x
}
const chunk = (x, n) => {
let ret = []
for(let i = 0; i < x.length; i+=n){
ret.push(x.substring(i,i+n))
}
return ret
}
const check = (e) => {
if (document.forms[0].username.value === "admin") {
if (swap(chunk(document.forms[0].password.value, 30)).join("") == "7e08250c4aaa9ed206fd7c9e398e2}actf{cl1ent_s1de_sucks_544e67ef12024523398ee02fe7517fffa92516317199e454f4d2bdb04d9e419ccc7") {
location.href = "/win.html"
}
}
}
根据题意是把密码每30个字符分为一组,然后通过swap函数交换四段字符位置,输出结果为7e08250c4aaa9ed206fd7c9e398e2}actf{cl1ent_s1de_sucks_544e67ef12024523398ee02fe7517fffa92516317199e454f4d2bdb04d9e419ccc7,先把四段字符分开看
7e08250c4aaa9ed206fd7c9e398e2}
actf{cl1ent_s1de_sucks_544e67e
f12024523398ee02fe7517fffa9251
6317199e454f4d2bdb04d9e419ccc7
按照swap函数的定义,这段字符原本的顺序是4132,所以正确的密码是
actf{cl1ent_s1de_sucks_544e67e6317199e454f4d2bdb04d9e419ccc7f12024523398ee02fe7517fffa92517e08250c4aaa9ed206fd7c9e398e2}
即flag
directory
纯爆破,在burpsuite中用Intruder模块爆破,在3054.html找到flag
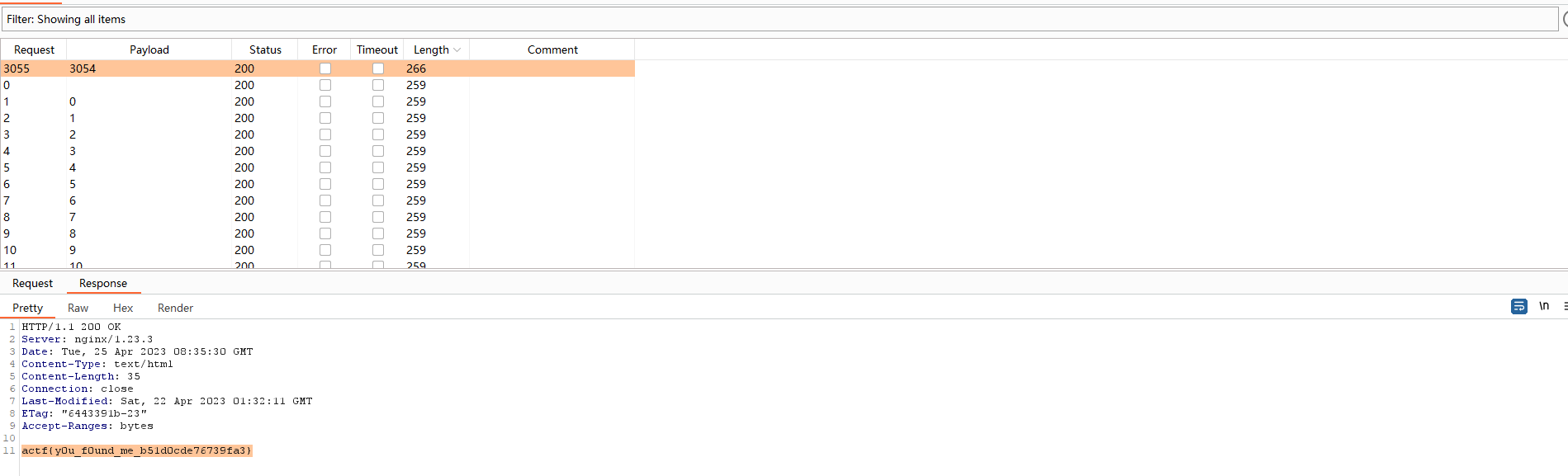
actf{y0u_f0und_me_b51d0cde76739fa3}
Celeste Tunneling Association
查看源码:
# run via `uvicorn app:app --port 6000`
import os
SECRET_SITE = b"flag.local"
FLAG = os.environ['FLAG']
async def app(scope, receive, send):
assert scope['type'] == 'http'
headers = scope['headers']
await send({
'type': 'http.response.start',
'status': 200,
'headers': [
[b'content-type', b'text/plain'],
],
})
# IDK malformed requests or something
num_hosts = 0
for name, value in headers:
if name == b"host":
num_hosts += 1
if num_hosts == 1:
for name, value in headers:
if name == b"host" and value == SECRET_SITE:
await send({
'type': 'http.response.body',
'body': FLAG.encode(),
})
return
await send({
'type': 'http.response.body',
'body': b'Welcome to the _tunnel_. Watch your step!!',
})
可知,要求请求中host值为flag.local获得flag,hackbar发包不成功,用python写个脚本发包获取flag:
import requests
headers = {
"Host": "flag.local"
}
response = requests.get("https://pioneer.tailec718.ts.net/", headers=headers)
print(response.text)
actf{reaching_the_core__chapter_8}
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至1004454362@qq.com